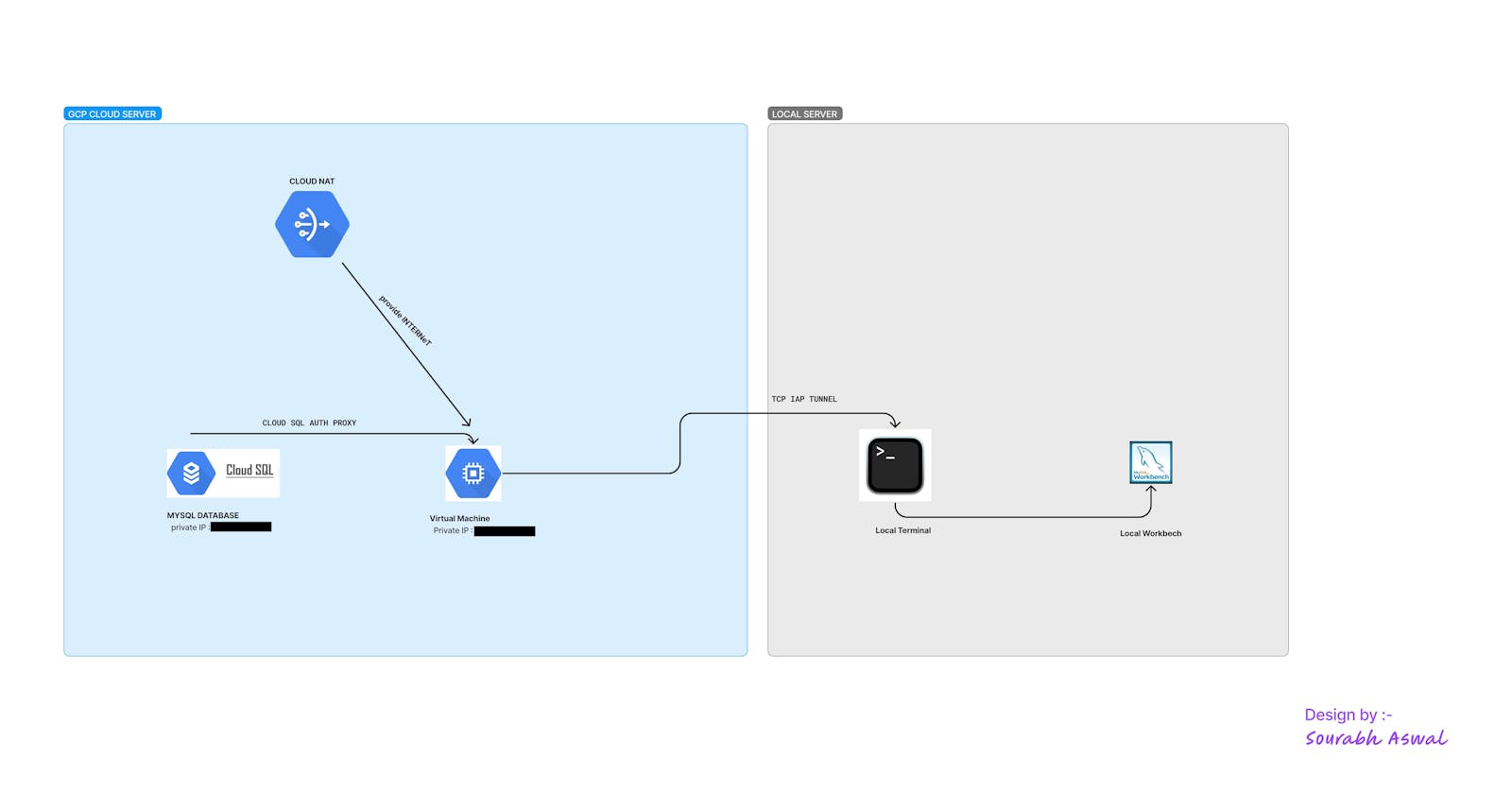
Private Cloud Sql Connection / Cloud Nat / Private Compute Engine / Mysql Workbench / Cloud Run / VPC
PRIVATE CLOUD SQL
Create sql database with private ip and default vpc and network (10.111.112.0/20)
PRIVATE COMPUTE ENGINE
1 :- Create a virtual machine with private ip
2 :- Create a service account with cloud-sql-client-proxy permission
SSH
1:-Download cloud sql proxy for vm :- curl -o cloud-sql-proxy https://storage.googleapis.com/cloud-sql-connectors/cloud-sql-proxy/v2.7.1/cloud-sql-proxy.linux.amd64
2 :- give that a permision :- chmod +x cloud-sql-proxy
3 :- vim cloud-credential.json
4 :- ./cloud-sql-proxy --address 0.0.0.0 --port 3306 vertical-set-xyz:us-central1:xyzpriavtedb --private-ip 10.111.122.60 --credentials-file=/home/sourabhaswal/cloud-credential.json
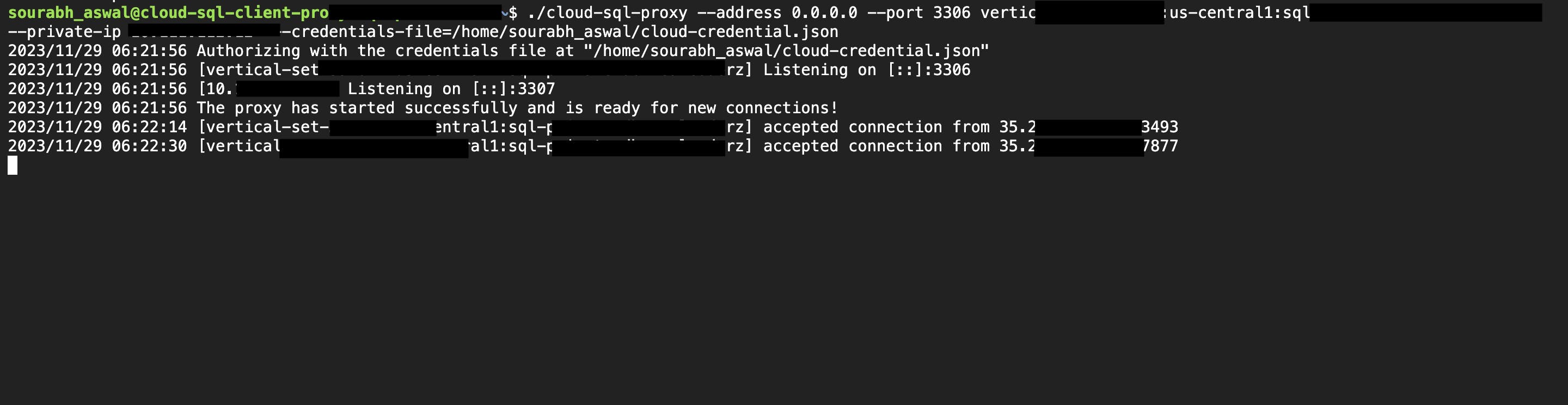
CLOUD NAT
Cloud NAT, Google Cloud's managed network address translation service, enables you to provision your application instances without public IP addresses while also allowing them to access the internet—for updates, patching, config management, and more—in a controlled and efficient manner
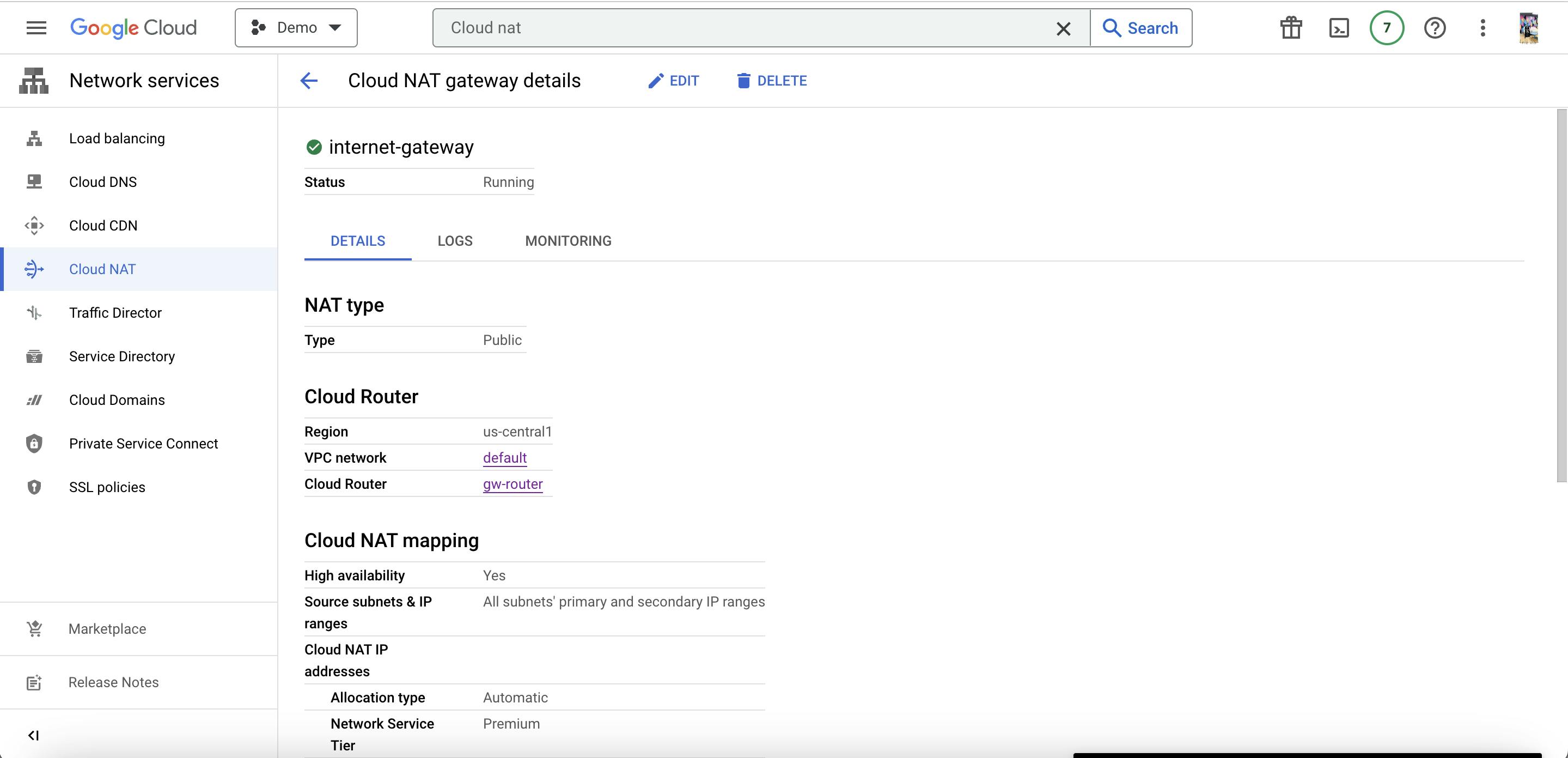
LOCAL TERMINAL
Connect server to local through iap tunneling
gcloud compute start-iap-tunnel cloud-sql-client-vm 3306 --local-host-port=localhost:9090 --zone=us-central1-a
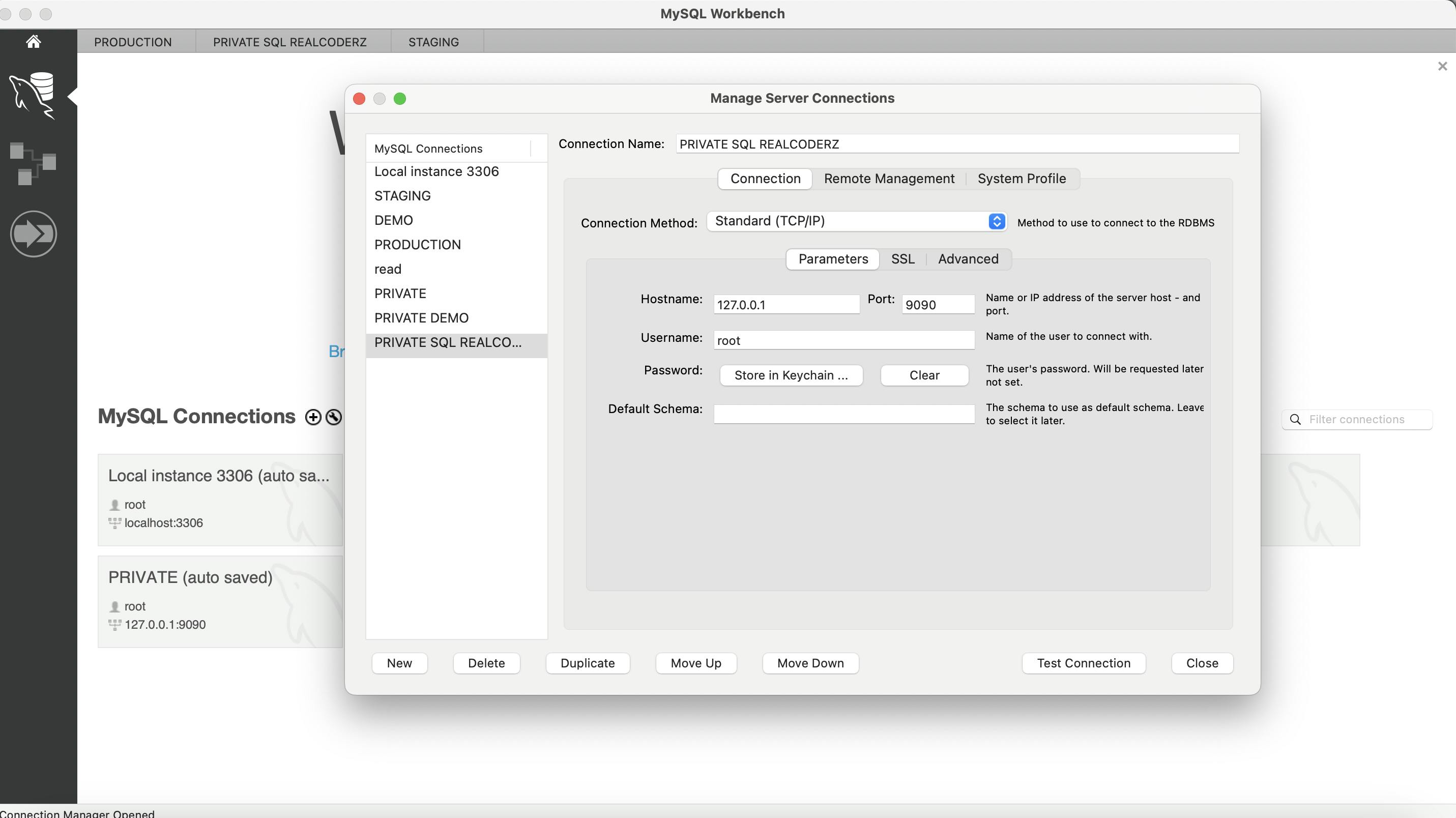
MYSQL WORKBENCH LOCALLY
Create VPC connector for making connection with Cloud Run Service
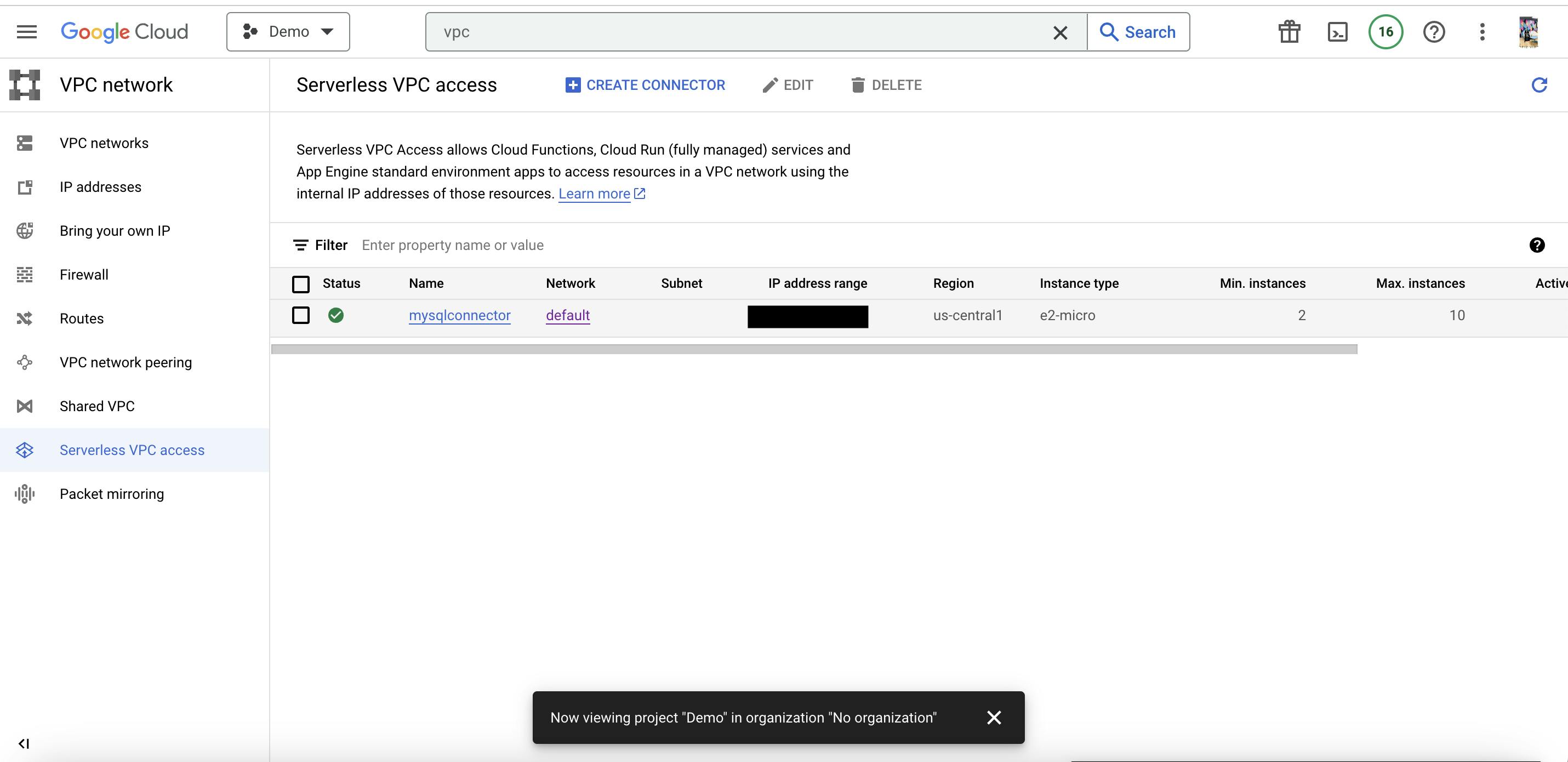
Deploy application with configure networking with vpc connector which we create earlier