Open source secrets management platform used for storing and managing your secrets , this includes credentials , access token certificates , encryption keys or anything that your secrets .
Vault is primarily used to secure application workloads such as authentication between apis and where no human are involved .
Need Ubuntu server instance in AWS cloud with open security group for port 8200
Hashicorp vault installation
1 - Installation
2 - Start and Stop
3- UI , Production Env .
INSTALLATION
curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo gpg --dearmor -o /usr/share/keyrings/hashicorp-archive-keyring.gpg
echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com focal main" | sudo tee /etc/apt/sources.list.d/hashicorp.list
sudo apt update
sudo apt install vault
sudo systemctl start vault
sudo systemctl enable vault
vault --version
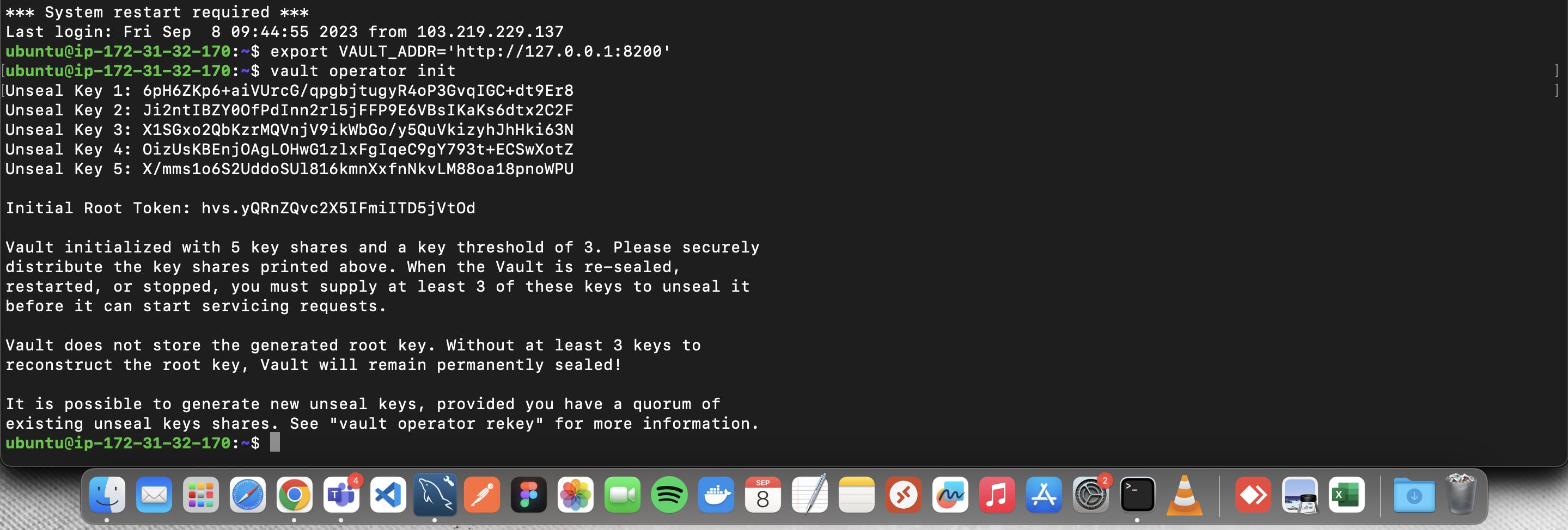
Save unseal key and token
Unseal Key: Zvbpxnl+yMomzq/CSwcCpcBaOBxB48VWn/HY+WD24h4=
Root Token: hvs.1eHWxNToLBYVvrKF10Ahb561
START and STOP VAULT server
export VAULT_ADDR='http://127.0.0.1:8200' export VAULT_TOKEN="hvs.1eHWxNToLBYVvrKF10Ahb561" vault status

DEPLOY VAULT IN PRODUCTION
1- Stop vault in development mode CTRL + C
2 - Unset vault Token $ unset VAULT_TOKEN
3 - Create vault configuration
create directory $ mkdir -p ./vault/data
touch config.hcl
vim config.hcl
storage "raft" { path = "./vault/data" node_id = "node1" } listener "tcp" { address = "0.0.0.0:8200" tls_disable = "true" } api_addr = "http://127.0.0.1:8200" cluster_addr = "https://127.0.0.1:8201" ui = true
4 - Starting vault server
$ vault server -config=config.hcl
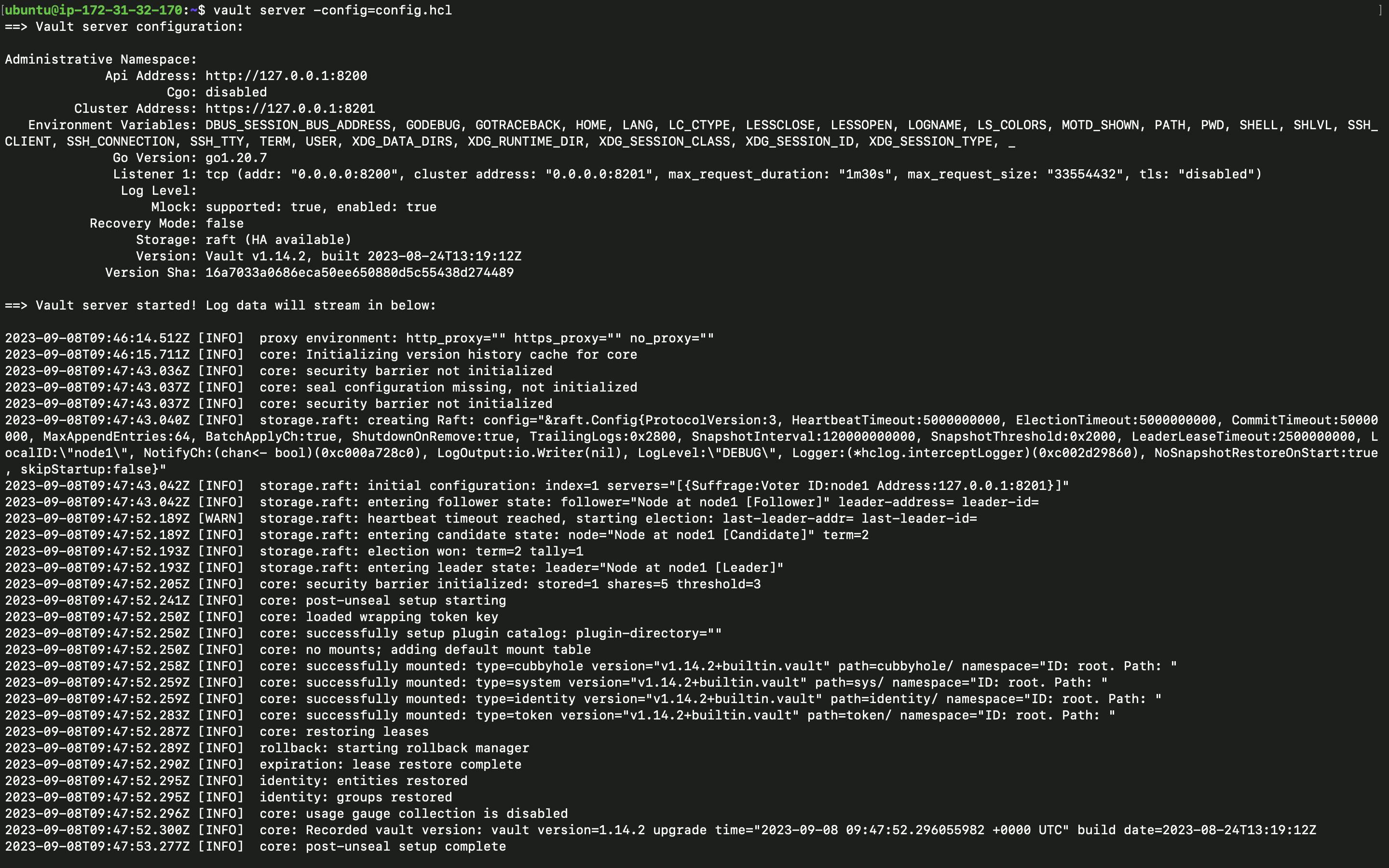
5 - Export vault address
$ export VAULT_ADDR="http://127.0.0.0:8200"
6 - Initialize vault
$ vault operator init
# SEAL / UNSEAL
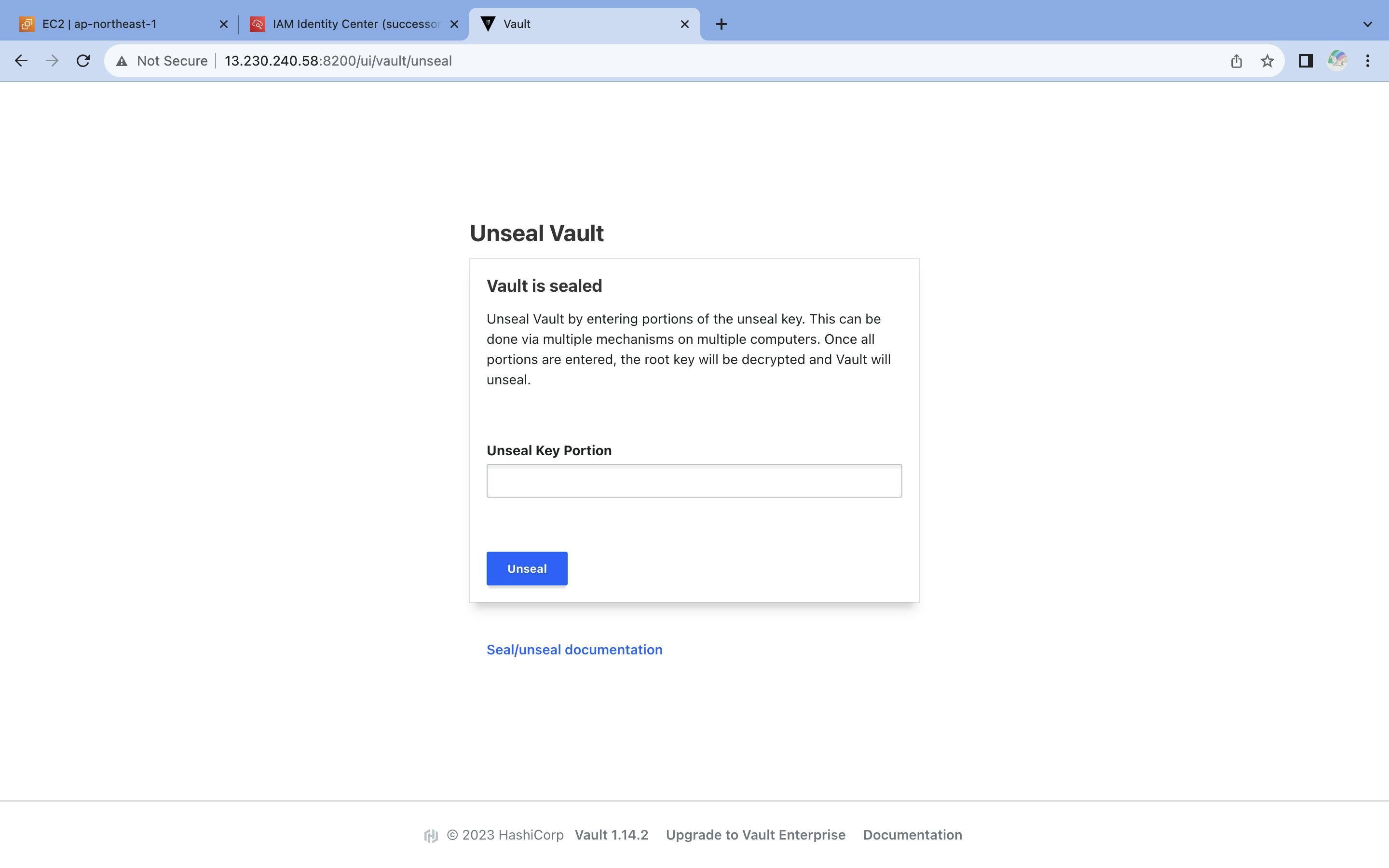
Put unseal key ( which we get from vault operator init ) three time in a row , to unseal the vault
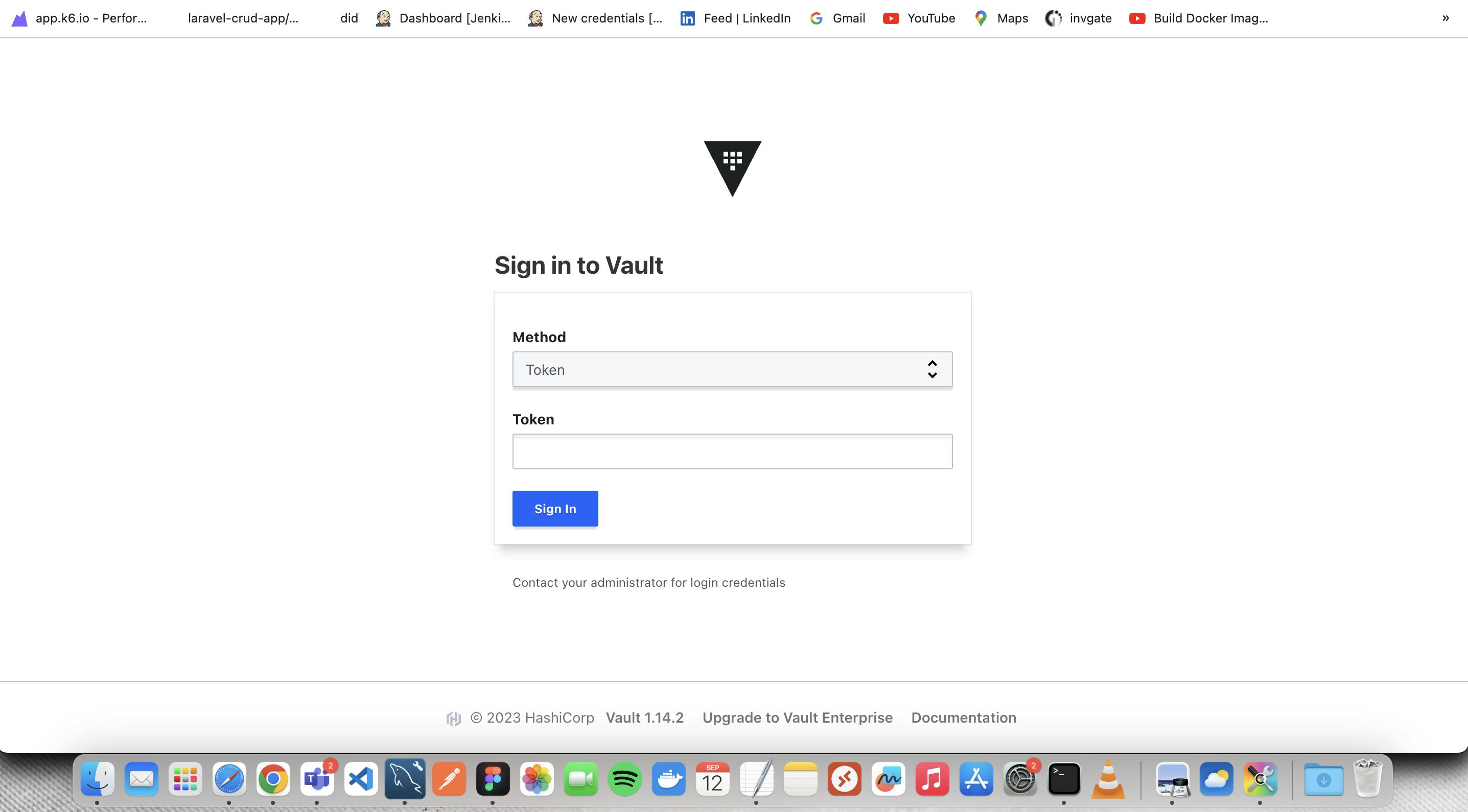
Put Initial root token in it
Dashboard :
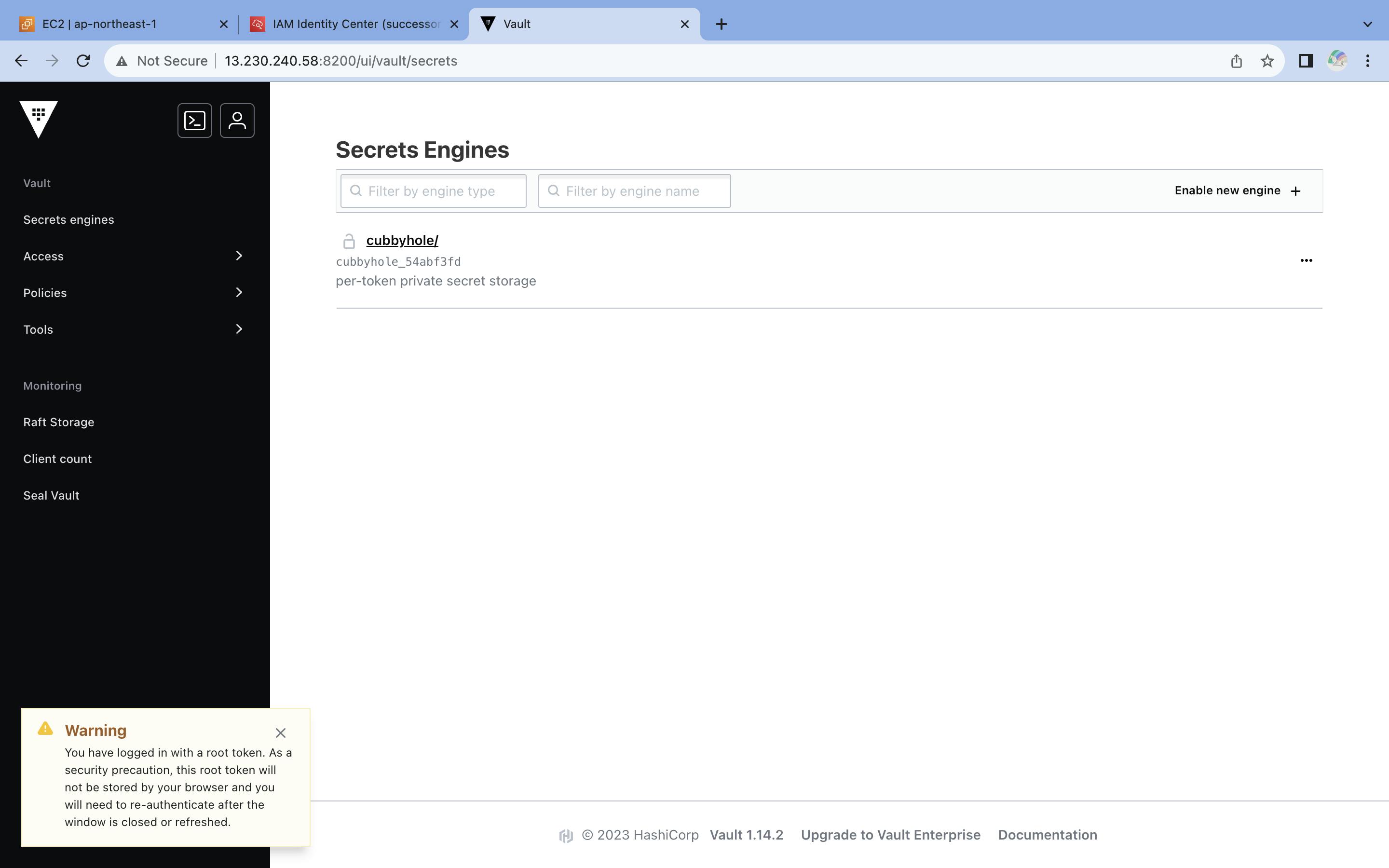
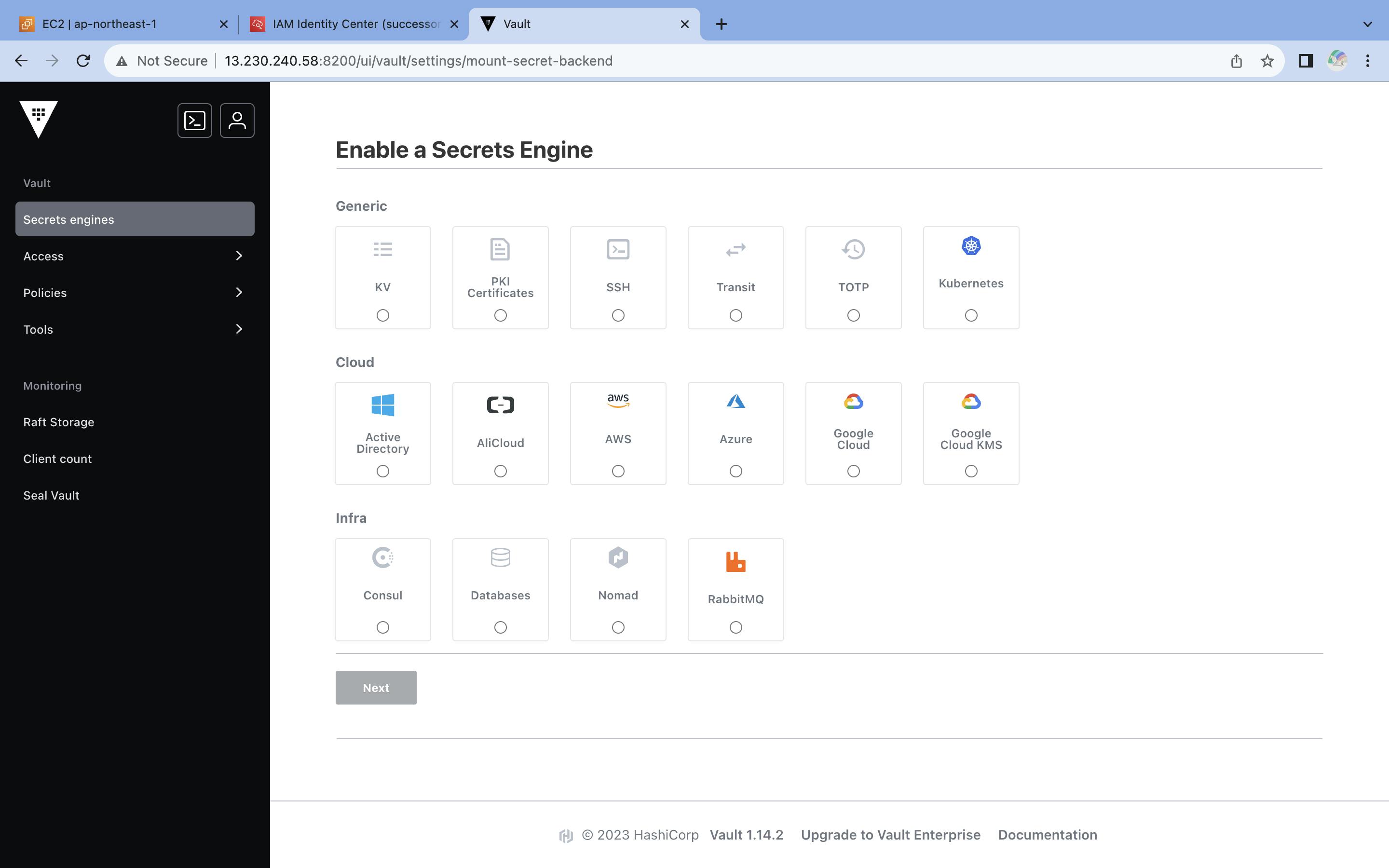
Where you can enable new engine
These are some Secrets Engine